‘.locky File Extension’ Ransomware Description
Ransomware Infections have become increasingly common in the last few years. Only in the first two months of 2016, computer users have come across hundreds of new ransomware infections and variants of previous ransomware threats. One of the most prevalent threats in this period is TeslaCrypt 3.0, a new version of a ransomware Trojan first released in early 2015. The '.locky File Extension' Ransomware is one of the many variants of this threat. This new version of TeslaCrypt closes a loophole that allowed computer users to help computer users recover their files previously. Variants of this threat have been released, each changing the victims' files' extensions to a different string. In the case of the '.locky File Extension' Ransomware Trojan, this is a TeslaCrypt 3.0 variant that changes encrypted files' extensions to LOCKY.
How the '.locky File Extension' Ransomware may Infect a Computer
The '.locky File Extension' Ransomware infection process is not difficult to understand. In fact, most encryption ransomware tends to follow the same approach when infecting a computer. First, the '.locky File Extension' Ransomware will be delivered using common threat delivery methods, in most cases a corrupted email attachment contained in a phishing email message. When the victim opens the harmful email attachment, the '.locky File Extension' Ransomware is installed on the victim's computer. The '.locky File Extension' Ransomware will perform a scan of the victim's computer, looking for files to encrypt using its AES encryption algorithm. The .locky File Extension' Ransomware Trojan will infect files with the following extensions:
.7z; .rar; .m4a; .wma; .avi; .wmv; .csv; .d3dbsp; .sc2save; .sie; .sum; .ibank; .t13; .t12; .qdf; .gdb; .tax; .pkpass; .bc6; .bc7; .bkp; .qic; .bkf; .sidn; .sidd; .mddata; .itl; .itdb; .icxs; .hvpl; .hplg; .hkdb; .mdbackup; .syncdb; .gho; .cas; .svg; .map; .wmo; .itm; .sb; .fos; .mcgame; .vdf; .ztmp; .sis; .sid; .ncf; .menu; .layout; .dmp; .blob; .esm; .001; .vtf; .dazip; .fpk; .mlx; .kf; .iwd; .vpk; .tor; .psk; .rim; .w3x; .fsh; .ntl; .arch00; .lvl; .snx; .cfr; .ff; .vpp_pc; .lrf; .m2; .mcmeta; .vfs0; .mpqge; .kdb; .db0; .DayZProfile; .rofl; .hkx; .bar; .upk; .das; .iwi; .litemod; .asset; .forge; .ltx; .bsa; .apk; .re4; .sav; .lbf; .slm; .bik; .epk; .rgss3a; .pak; .big; .unity3d; .wotreplay; .xxx; .desc; .py; .m3u; .flv; .js; .css; .rb; .png; .jpeg; .txt; .p7c; .p7b; .p12; .pfx; .pem; .crt; .cer; .der; .x3f; .srw; .pef; .ptx; .r3d; .rw2; .rwl; .raw; .raf; .orf; .nrw; .mrwref; .mef; .erf; .kdc; .dcr; .cr2; .crw; .bay; .sr2; .srf; .arw; .3fr; .dng; .jpeg; .jpg; .cdr; .indd; .ai; .eps; .pdf; .pdd; .psd; .dbfv; .mdf; .wb2; .rtf; .wpd; .dxg; .xf; .dwg; .pst; .accdb; .mdb; .pptm; .pptx; .ppt; .xlk; .xlsb; .xlsm; .xlsx; .xls; .wps; .docm; .docx; .doc; .odb; .odc; .odm; .odp; .ods; .odt
After the '.locky File Extension' Ransomware has infected the victim's files, the '.locky File Extension' Ransomware will change the affected files' extensions to LOCKY to indicate which files have been encrypted. The '.locky File Extension' Ransomware will also delete Shadow Volume copies of encrypted files as well as System Restore points, making it impossible for computer users to use alternate methods to recover their files. Sadly, it is currently not possible to decrypt the files encrypted by the '.locky File Extension' Ransomware without the encryption key, which is stored on the Command and Control server rather than in the '.locky File Extension' Ransomware infection itself.
The '.locky File Extension' Ransomware alerts the victim of the infection using text or image files dropped on the victim's computer. These messages will demand payment of a ransom worthing several hundred dollars through BitCoin or other anonymous methods. The following is an example of a ransom message commonly associated with the '.locky File Extension' Ransomware:
Your personal files are encrypted!
Your files have been safely encrypted on this PC: photos, videos, documents, etc. Click "Show Encrypted Files" button to view a complete list on encrypted files, and you can personally verify this.
Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt files you need to obtain the private key.
Step 1 - Uninstall .locky File Extension From Win 10 /Win 8/Win 7/Vista/XP
Open Control Panel On Windows 10
- Click Start Menu >> click Settings
- Double-click System
- Click Apps & features >> Select .locky File Extension or related harmful program >> Click Uninstall when the button appears
Open Control Panel On Win 8
- Click the File Explorer icon on the bottom left corner of desktop to open Libraries window.
- Click Desktop in right side bar >> double click Control Panel
Open Control Panel On Windows 7/Vista/XP
- Click Start Menu >> Click Control Panel
Removal Of .locky File Extension From Control Panel
- In Control Panel, click Uninstall a program
- Click Installed On tab to find out .locky File Extension and unwanted programs >> Click Uninstall button after selecting a program
Step 2 - Clear up malicious files of .locky File Extension in Registry
- Press Windows + R keys at the same time to open Run window
- Type regedit and click OK :
- Locate and clear up the malicious registry files of .locky File Extension virus:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciessystem “DisableTaskMgr” = ‘1'
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\[virus name]
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerDownload “CheckExeSignatures” = ‘no’
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain “Default_Page_URL”
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerAdvanced “ShowSuperHidden” = 0'
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Tracing\Muvic_RASAPI32
HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\SETTINGS\{RANDOM}
Reset your homepage page To Remove .locky File Extension Virus
Reset Microsoft Edge Browser
- Select More (…) on the address bar, then Settings
- Under Open with, select A specific page or pages
- select Custom to enter the URL of page you want to set as homepage
Reset IE Browser
- Open Internet Explorer.
- Click the Tools button, and then click Manage add-ons.
- Click Toolbar and Extensions, then select .locky File Extension and related extensions and click Disable
Reset Firefox Browser
- Click the menu button and choose Add-ons to open Manager tab
- In the Add-ons Manager tab, select the Extensions or Appearance panel.
- Select the .locky File Extension and related add-on you need to remove.
- Click the Remove button.
Reset Chrome Browser
- Click the hamburger menu icon on the Google Chrome toolbar and then More tools.
- Select More tools from the menu.
- Select Extensions from the side menu
- Click the trash can icon link next to .locky File Extension extension or related extension you wish to remove.
Download Automatic .locky File Extension Removal Tool
If you are not able to remove .locky File Extension virus manually from your computer system or you are getting any problem in removing this threat from your PC then you are advised to use Automatic Removal Tool. it is an advanced and powerful malware removal tool that can easily delete all kind of harmful threats and malware from your system. You can download the trial version of this tool to detect .locky File Extension virus on your PC. Once you feel satisfied with the detection then you can purchase this program to remove the threat permanently.
How To Remove .locky File Extension With Automatic Removal Tool
Step 1 - Install the software on your computer and click scan computer now button

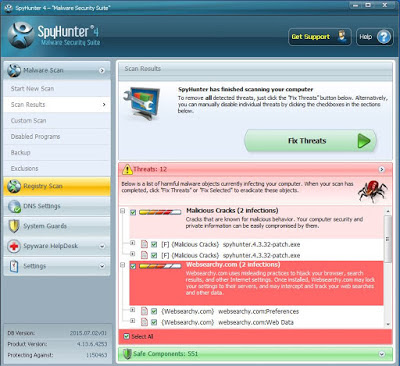
Step 2 - Click on Fix Threats Now to remove all detected viruses or malware.
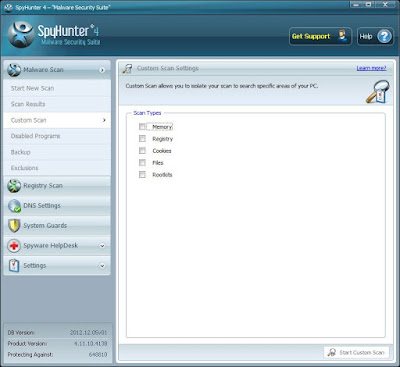
Step 3 - Use Custom Scan feature to scan any specific part of computer.
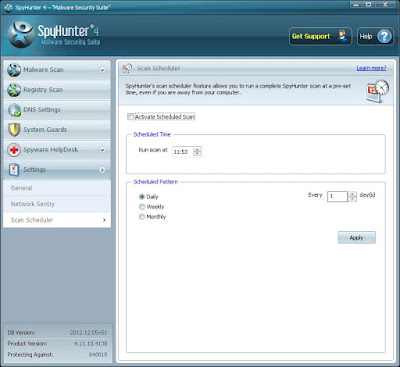
Step 4 - Configure Scan Scheduler option to ensure the safety of your PC.

I managed to remove it by using MalwareFox, it was rather easy if you ask me.
ReplyDeleteYoBit lets you to claim FREE COINS from over 100 distinct crypto-currencies, you complete a captcha once and claim as many as coins you can from the available offers.
ReplyDeleteAfter you make about 20-30 claims, you complete the captcha and continue claiming.
You can click claim as much as 50 times per one captcha.
The coins will safe in your account, and you can convert them to Bitcoins or any other currency you want.