Do you know what JuicyLemon Ransomware is?
JuicyLemon Ransomware is an obnoxious infection that can slither into your Windows operating system without any warning. According to our research, this malicious threat is currently spread using the Angler Exploit Kit, and its executable is either downloaded in %APPDATA% or %TEMP% folders. This .exe file is represented with an icon of a purple folder, and its name is misleading (e.g., WebCam.exe) to make it more difficult for you to detect and delete it. If you remove JuicyLemon Ransomware file before it initiates file encryption, you might be able to stop all malicious processes. Unfortunately, because this threat is spread silently, most users realize that it is active only after their personal files get encrypted. When that happens, the malicious ransomware automatically deletes itself, and there is little to be done. Of course, there are things that need to be discussed, and we suggest reading this report.
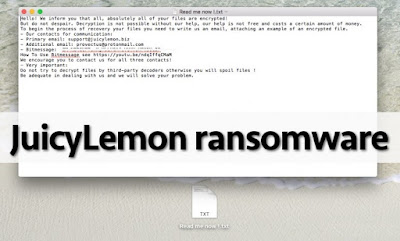

According to our research, JuicyLemon Ransomware is a fairly new infection, and we are hopeful that not many users have fallen victim to it. It is extremely important to keep yourself guarded against this threat because it can encrypt personal files, and this is one of the worst things that can happen because decrypting these files is often impossible. Once the ransomware is done encrypting files, it creates a text file on the Desktop with a completely random name (e.g., P1AD0H2NPVY3MARJT.txt). This text file represents the demands of the creators of this malicious ransomware. Users are instructed to contact cyber criminals via one of the available emails (support@juicylemon.biz or provectus@protonmail.com) or using the Bitmessage system. Once you communicate with cyber criminals – and you should not do that using your main email address – you will receive additional instructions on how to pay a ransom. Whether the ransom demanded for the decryption services is small or big, you have to think carefully about paying it as there is a risk that your payment will be taken with nothing in return.
