Do you know what is UltraCrypter? We classify it as a ransomware. It is easy to find out that your PC is infected with UltraCrypter and the sign is obvious. When your system gets this item inside, all your files will be encrypted at first, and then it will blackmail the users to pay for huge amount of money to rescue these files. That is the main task of ransomware. If you continue to keep it on your PC, such tragedy will occur time by time. Therefore, we advice you to learn more about this malicious stuff and get rid of it with the instruction here.
UltraCrypter is an updated version of CryptXXX ransomware. As with CryptXXX, UltraCrypter is distributed using the Angler Exploit Kit. In fact, these viruses are practically identical. UltraCrypter uses an asymmetric RSA-4096 algorithm to encrypt many of the files stored on the infiltrated system. Therefore, public (encryption) and private (decryption) keys are generated and are stored on remote servers. Decryption without the private key is impossible. Furthermore, UltraCrypter adds a .cryp1 extension to the name of each encrypted file. Following successful encryption, UltraCrypter generates three different files: .bmp (which is also set as the desktop wallpaper); .txt, and; .html. These files have an identical naming format - [Victim’s personal ID].
They also contain an identical message stating that files have been encrypted and that the victim must pay a ransom to download a decryption tool. To receive detailed payment instructions, users must visit a Tor browser link provided. The size of ransom is equivalent to 1.2 Bitcoin ($567.6). If this is not paid within the given time frame, it will double to 2.4 BTC. Specifying a certain time frame and increasing the size of ransom if not paid is behavior common to ransomware-type viruses. UltraCrypter allows victims to decrypt one selected file free of charge - this is to prove that the encryption is possible. CryptXXX and UltraCrypter attempt to mimic the CryptoWall and TeslaCrypt viruses. Unfortunately, there currently are no tools capable of restoring files encrypted by UltraCrypter. Viruses such as UltraCrypter are one of the main reasons why you should maintain regular data backups, since the only other solution is to restore your files and/or system from a backup.
Research shows that ransomware-type viruses have similar characteristics. In fact, all have identical behavior - they encrypt files and demand ransom payments. Locky, Cerber, zCrypt, Zyklon, and BadBlock are just some examples from many. The only noticeable differences are type of algorithm used to encrypt and size of ransom. Research also shows that many cyber criminals ignore victims even if they pay the ransom. Paying does not guarantee that your files will ever be decrypted. Therefore, you should never pay or attempt to contact these criminals. Furthermore, ransomware is often distributed using malicious email attachments, deceptive application updates, peer-to-peer (P2P) networks, and trojans. For these reasons, keeping your installed software up-to-date and using a legitimate anti-virus/anti-spyware suite is very important. In addition, never open any attachments sent from suspicious and/or unrecognized email addresses. We also strongly advise you to download your chosen files/applications from trusted sources only (for example, official download websites).
How does UltraCrypter Ransomware Locate on Your Computer?
First and foremost, UltraCrypter ransomware trojan is spread through spam e-mails and their attachments pretending to be official letters from official institutions or companies (e.g. from Tax Inspectorate, etc.). Either the links in the e-mails or their attachments are infected with malicious codes. This crypto-virus is distributed by exploits kits as well, namely, Angler EK and Bedep EK. These hacking tools targets Java and Adobe Flash Player vulnerabilities to inject malware.
How to Decrypt Files Encrypted by UltraCrypter Ransomware?
Alas, there are no decryptions tools available at the moment. Kaspersky has developed working decryptors for the previous versions of this ransomware. At the moment security experts are working hard on this. Yet you can apply data recovery tools such as the products of the same Kaspersky Lab, R-studio or others. UltraCrypter file encryptor deletes Shadow Volume Copies. Thus, you will not be able to use Shadow Volume Copy Service. We highly recommend to back up your data in external hard drives or to make use of external storage services (e.g. Cloud Storage, etc.) in the future. To remove this ransomware virus employ reputable malware removal software such as SpyHunter, Malwarebytes or StopZilla. Follow the removal guide of UltraCrypter ransomware below.
Step 1 - Uninstall CryptXXX ransomware From Win 10 /Win 8/Win 7/Vista/XP
Open Control Panel On Windows 10
- Click Start Menu >> click Settings
- Double-click System
- Click Apps & features >> Select CryptXXX ransomware or related harmful program >> Click Uninstall when the button appears
Open Control Panel On Win 8
- Click the File Explorer icon on the bottom left corner of desktop to open Libraries window.
- Click Desktop in right side bar >> double click Control Panel
Open Control Panel On Windows 7/Vista/XP
- Click Start Menu >> Click Control Panel
Removal Of CryptXXX ransomware From Control Panel
- In Control Panel, click Uninstall a program
- Click Installed On tab to find out CryptXXX ransomware and unwanted programs >> Click Uninstall button after selecting a program
Step 2 - Clear up malicious files of CryptXXX ransomware in Registry
- Press Windows + R keys at the same time to open Run window
- Type regedit and click OK :
- Locate and clear up the malicious registry files of CryptXXX ransomware virus:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciessystem “DisableTaskMgr” = ‘1'
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\[virus name]
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerDownload “CheckExeSignatures” = ‘no’
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMain “Default_Page_URL”
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerAdvanced “ShowSuperHidden” = 0'
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Tracing\Muvic_RASAPI32
HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXT\SETTINGS\{RANDOM}
Reset your homepage page To Remove CryptXXX ransomware Virus
Reset Microsoft Edge Browser
- Select More (…) on the address bar, then Settings
- Under Open with, select A specific page or pages
- select Custom to enter the URL of page you want to set as homepage
Reset IE Browser
- Open Internet Explorer.
- Click the Tools button, and then click Manage add-ons.
- Click Toolbar and Extensions, then select CryptXXX ransomware and related extensions and click Disable
Reset Firefox Browser
- Click the menu button and choose Add-ons to open Manager tab
- In the Add-ons Manager tab, select the Extensions or Appearance panel.
- Select the CryptXXX ransomware and related add-on you need to remove.
- Click the Remove button.
Reset Chrome Browser
- Click the hamburger menu icon on the Google Chrome toolbar and then More tools.
- Select More tools from the menu.
- Select Extensions from the side menu
- Click the trash can icon link next to CryptXXX ransomware extension or related extension you wish to remove.
Download Automatic CryptXXX ransomware Removal Tool
If you are not able to remove CryptXXX ransomware virus manually from your computer system or you are getting any problem in removing this threat from your PC then you are advised to use Automatic Removal Tool. it is an advanced and powerful malware removal tool that can easily delete all kind of harmful threats and malware from your system. You can download the trial version of this tool to detect CryptXXX ransomware virus on your PC. Once you feel satisfied with the detection then you can purchase this program to remove the threat permanently.
How To Remove CryptXXX ransomware With Automatic Removal Tool
Step 1 - Install the software on your computer and click scan computer now button

Step 2 - Click on Fix Threats Now to remove all detected viruses or malware.
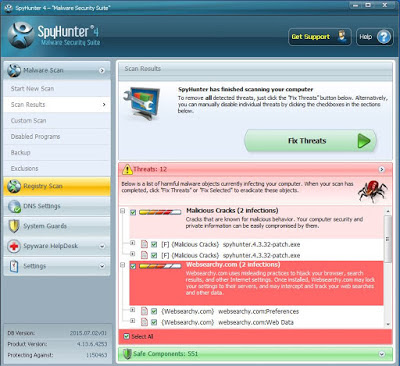
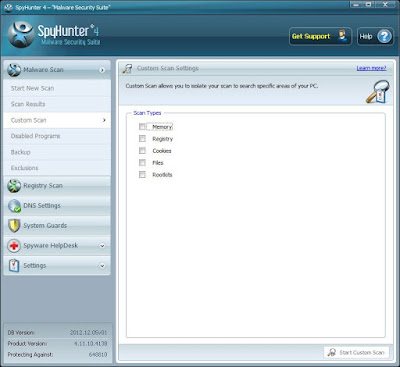
Step 3 - Use Custom Scan feature to scan any specific part of computer.
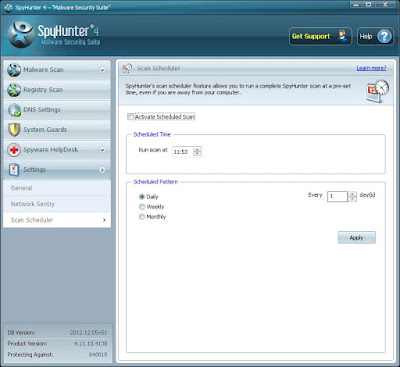
Step 4 - Configure Scan Scheduler option to ensure the safety of your PC.


BitKONG Test your bravery and earn bitcoins from the big bad kong.
ReplyDeleteTIP: Claim free bitcoins every 10 mins from the free faucet.
Claim free bitcoins over at Easy Bitcoin. 11 to 33 satoshis every 10 minutes.
ReplyDeleteIf you're trying to BUY bitcoins online, PAXFUL is the best source for bitcoins as it allows buying bitcoins by 100's of different payment methods, such as MoneyGram, Western Union, PayPal, Credit Cards and even exchanging your gift cards for bitcoins.
ReplyDelete