What is Payms ransomware
Payms virus is yet another example of ransomware. This threat was created based on Jigsaw virus code, which is reportedly on sale in Dark Web forums for 139 USD. This virus encrypts victim’s files and demands 150 USD, but if the victim does not pay within 24 hours, the ransom price increases to 225 USD. However, it seems that cyber criminals ask for way smaller ransoms than they used to because computer users are already aware of ransomware threats, and also the majority of them refuse to pay the ransom.


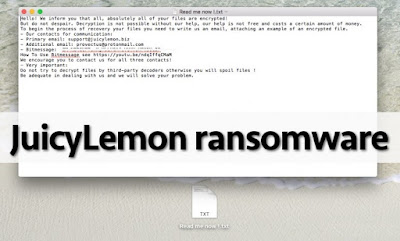
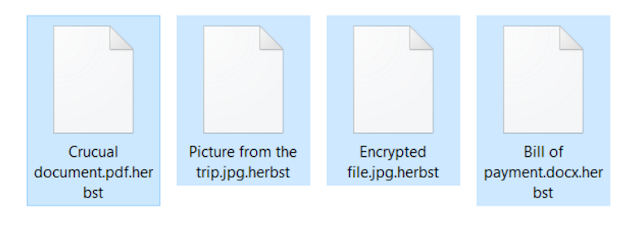
Payms ransomware adds .pay, .payms or .paymst file extensions to encrypted files, and leaves ransom notes in the computer system, called Payment_Instructions.txt. You can find a copy of this file on the desktop, as well as in all folders that contain some encrypted data. The ransom note informs the victim that all data on the computer has been encrypted, and there is no other way to decrypt it than to pay a ransom. The note is written in English and Spanish languages, and it also informs that if the victim attempts to tamper with the virus, all files will be deleted. It provides instructions on how to buy Bitcoins and says that the victim must transfer them to a provided address if he/she wants to access his/hers files ever again. According to crooks, they will eliminate the virus and decrypt the data after the payment is made.
Payms Ransomware – Distribution
Payms ransomware can distribute via a couple of ways. Your computer could get infected with the crypto-virus through spam e-mails which have an attachment with malicious code inside them. If the attachment is opened, malware might be injected inside your computer system. The file possibly has a name such as firefox.exe or something similar, so to try and trick you.
Past variants of the presently named Payms ransomware were delivered through social media sites and some file-share system, too. DropBox could still be a way of distribution as the original variant of the ransomware used that as well. Avoiding all suspicious files, links, and websites is a highly recommended action as there you might find malware such as this one.